What Are the 5 Most Overlooked Signs of Document Tampering?
Sreyan M Chowdhury | 31st December, 2025
4 min reads
Sreyan M Chowdhury | 31st December, 2025 | 4 min reads
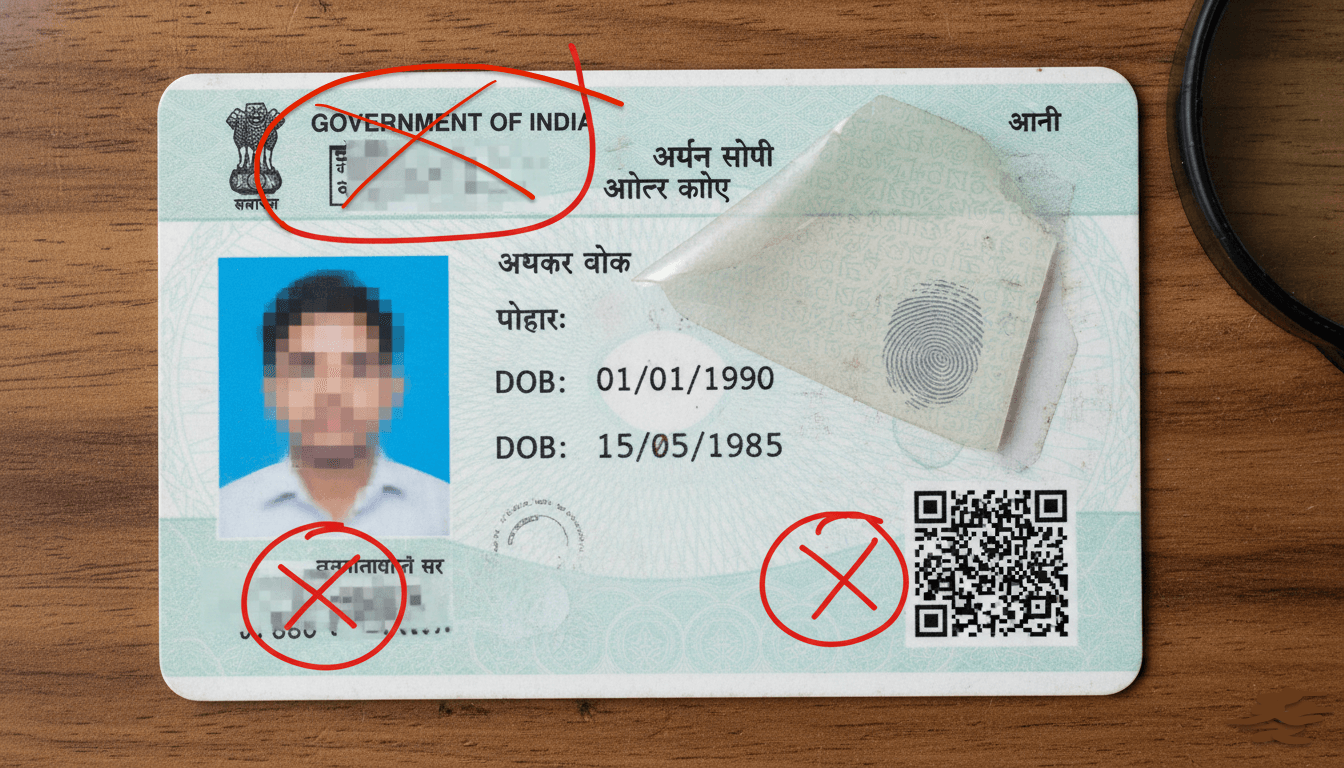
Imagine signing a contract only to find out later that your signature isn’t the only thing on the document that’s been altered. With digital forgeries skyrocketing, how can you spot the subtle signs of manipulation before it’s too late? This post uncovers the five most overlooked red flags and equips you with the knowledge—and tools—to protect your data.
Introduction: The Invisible Threat
Document tampering is a silent epidemic. In 2024, digital document forgeries accounted for 57% of all document fraud. A single undetected alteration can lead to severe financial loss or legal consequences. As forgeries grow more sophisticated, the human eye alone is no longer enough. This is why businesses are turning to document processing automation and AI document processing to identify tampering by detecting anomalies and validating data against trusted sources.
The 5 Overlooked Signs of Tampering
1. Inconsistent Signatures & Dates
Even slight variations in a signature’s slant, size, or pen pressure can indicate forgery. Similarly, look for:
Dates that appear altered or missing
Faint erasure marks or mismatched ink
Minor inconsistencies in handwriting style
2. Unusual Writing Patterns
Subtle changes in writing flow or pen pressure within a document can be a red flag. Signs include:
Hesitation marks or uneven letter spacing
Overlapping or cramped text
Variations in ink density on a single page
3. Metadata Manipulation (Digital Documents)
In digital files, metadata can be a hidden tell. Watch for:
Mismatched creation and modification dates
Discrepancies in author or software details
Suspicious file formatting or properties
4. Visual Inconsistencies in Digital Text
Advanced forgeries can alter text without obvious visual cues. However, subtle signs remain:
Slight font variations or pixel misalignments
Inconsistent spacing or baseline shifts
Artifacts from copy-paste or editing tools

5. Hash or Integrity Check Failures
When a document’s digital fingerprint (hash) doesn’t match the original, tampering is likely. This is especially relevant for:
Documents secured with blockchain timestamping
Files verified through integrity-checking platforms
Systems using document recognition software to validate against original versions
How Technology Is Revolutionizing Detection
Modern tools are closing the gap where human observation falls short:
AI & Dual-Path Recognition Networks: Advanced frameworks (like the two-stage dual-path network) detect text tampering with high accuracy by analyzing documents through multiple pathways.
Automated Hash & Blockchain Verification: Systems automatically compare document hashes and use blockchain timestamps to confirm authenticity, as highlighted in guides on how to detect document tampering.
Real-Time Validation Against Databases: AI-driven platforms cross-reference document data with third-party sources in real time, flagging discrepancies instantly.
Conclusion: Don’t Rely on the Eye Alone
Document tampering is evolving—but so are the solutions. By recognizing these five overlooked signs and implementing automated document processing, businesses can proactively safeguard their integrity. The next step? Evaluate your current document security and consider integrating AI-powered verification to stay ahead of forgers.
About the author
Sreyan M Chowdhury
Marketing Manager
Sreyan M Chowdhury | Marketing Manager
He is passionate about technology, automation, and SaaS. Blends creative strategy with data-driven insights to drive growth and streamline digital experiences. Always exploring new tech to stay ahead of the curve.
Interests: AI, Automation, SAAS
Content Overview
Share
FEATURED
Automation
Top 5 Best Field Service Management Software in 2025
Best Field Service Management Software
Shreyas R
27th November, 2023



